Account Opening Abuses
- David Senecal
- Nov 15, 2025
- 7 min read
Updated: Dec 7, 2025
Popular websites are often targeted by threat actors who open fake accounts in large numbers. This is known as account opening abuse, account creation fraud, or new account fraud. Fake accounts are primarily used for promotional abuse by scalpers, for example during sales events of limited edition items like concert tickets, sneakers, or the popular Pokemon cards. Fake accounts are also used as part of elaborated fraud schemes on gaming platforms, banks, and social medias. In this articles, we'll review the techniques used by threat actors to create those fake account. Part of this articles was first published in Akamai Technologies' blog website and also included in my book, The Reign of Botnets (Wiley),

Fraud rings: Cybercriminal collaboration
Fraud rings are common in the realm of account opening abuse, in which cybercriminals join forces to maximize their illicit gains. These rings consist of individuals or groups with specialized roles that contribute to different stages of the fraudulent account creation process. Fraudsters carry out account opening abuse in various ways, but generally start by collecting stolen PII, like names and addresses. The data generally come from various data breaches and can be bought easily on specialized web forums for hackers — both on the regular web and the dark web. Bots are typically employed to execute these attacks, allowing fraudsters to rapidly create multiple accounts.
The validation process
Account creation workflow varies in complexity, depending on a site’s validation process:
Lower complexity: Some sites want to avoid friction as much as possible and only validate that the selected username doesn’t already exist in the system.
Average complexity: Most sites validate at least the email address provided.
Higher complexity: Banks and fintech also validate the PII supplied to open the account.
Let’s take a closer look at different scenarios and see how attackers exploit logic flaws and use other techniques to create fraudulent accounts.
Sites without email verification
In the simplest use case (Figure 1), opening an account requires very little validation beyond confirming that the same username doesn’t already exist on the site. In this situation, the attacker doesn’t need valid inboxes and can simply create random accounts on the site at will.
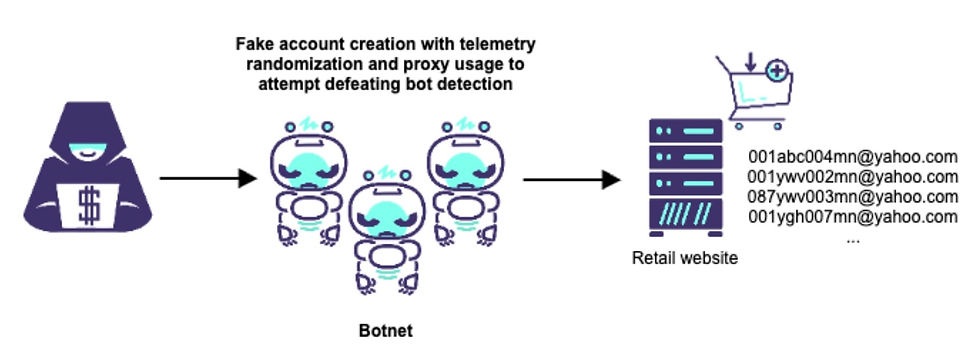
Fig. 1: A fraudster can use invalid email addresses when the site doesn’t enforce email validation
Sites with email verification
When email verification is enforced, the attacker must supply a valid email address for verification. Harvesting valid inboxes on legitimate email systems and harvesting fake accounts on various websites is too much for one actor – that’s where the fraud ring comes into play (Figure 2).

Fig. 2: Account opening abuse with email validation
Email inboxes for sale
In the fraud world, like in the legitimate world, each fraudster has their specialty and sells the product of their labor (credentials) to others. A new account fraudster specializes in harvesting inboxes on legitimate email platforms, which are then sold in bulk on the dark web marketplace (Figure 2, steps 1 and 2). An example of such a provider is the now defunct hotmailbox.me (Figure 3), a subsidiary of 1stcaptcha.com, which was based in Vietnam. They use their CAPTCHA-solving technology to harvest new accounts from major email services protected with CAPTCHA products.

Fig. 3: hotmaibox.me resells Outlook email accounts
Fraudsters interested in creating fake accounts on various sites can acquire these inboxes (Figure 2, step 3) and use them as part of their account creation process. Based on the current price, one can buy 1,000 accounts for approximately $2.20.
Procuring disposable inboxes
Alternatively, an attacker may decide to procure disposable inboxes (Figure 4) through sites like TempMail, Dispostable (Figure 2, step 3), or another similar service. The primary purpose of disposable or temporary email services is to help legitimate users preserve their privacy when creating a new account online. But like many privacy-oriented services, they are also commonly used by fraudsters.

Fig. 4: dispostable.com is a disposable email service portal
Creating random domains to generate fake accounts
Another technique involves creating random domains with mail exchange (MX) records through platforms like GoDaddy, Google Domains, Squarespace Domains, or similar services. Google simplifies the process by letting users easily link domains to valid Gmail accounts, facilitating the creation of hundreds of domains. Figure 5 shows an example of an attack in which a dozen domains are used to generate hundreds of accounts. Attackers may use hundreds of domains for an attack campaign and distribute the attack traffic evenly. The broad domain distribution makes it impossible for defenders to block based on the email domain. As seen in the figure, the accounts opened with disposable domains are very sporadic and only last a few minutes at a time. The distribution column in Figure 5 represents the activity seen on each domain over a 7 days period.

Fig. 5: Large attack using several disposable email domains
Once the inboxes are ready, the attacker leverages a botnet to handle both the account creation and the verification step (Figure 2, step 4). The list of fake accounts may be used directly by the attacker or offered for sale on the dark web marketplace for other fraudsters to carry out their own schemes (Figure 2, step 5).
Understanding more complex registration workflows
For banking sites or sites that require a subscription, users must provide more information about their identity, including home address, government-issued ID, and phone number. The site will verify the email address and the other information with some level of scrutiny. Fraudsters who want to create new bank accounts need reasonably valid and verifiable data. In this case, the attacker is not likely to use disposable emails since they would be too obvious an anomaly for the bank security team to miss. The attacker is more likely to use regular email services like Gmail or Microsoft Outlook (Figure 6) for this kind of attack. In this scenario, two different fraudsters may supply information upstream:
One will supply valid inboxes (Figure 6, steps 1 and 2)
The other will supply PII that may have been harvested through major data leaks (Figure 6, step 3)
Fraudsters who open bank accounts and take advantage of promotional offers acquire both datasets from the dark web and combine them to create a synthetic identity (Figure 6, step 4).

Fig 6: Account opening abuse ring for more complex registration workflows
For websites that require phone verification to open an account, the fraudster would generally provide their own mobile phone number. The more advanced account verification step can then be carried out through human labor.
Detecting Account Opening Abuses
Since bots are commonly used in this attack, a bot management product can help detect the activity. However is is also recommended to use email intelligence methods that evaluates the address used to open the account can help detect more complex low and slow attacks. The email address consists of the email local- part or handle and the email domain, separated by the @ sign: local-part@domain. For example, john_doe@example.com, where john_doe is the email local part, and example.com is the email domain. As noted previously, fraudsters create thousands of fake accounts. Each account created requires a unique email address. Considering the sheer volume of emails required, fraudsters often develop email address generators, which, depending on their sophistication, may present some apparent anomalies compared to legitimate accounts. The following table includes a few concrete examples of legitimate email addresses:
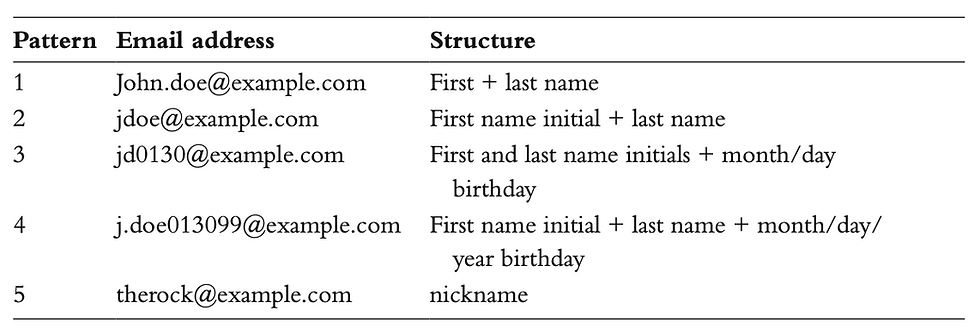
In contrast, fraudsters who want to create fake accounts don’t always follow this model.
The randomization techniques they use for the email address local-part may include the following patterns:

Detecting Randomization Patterns
Email address syntax validation methods, also known as email intelligence, can help extend what bot manager products can detect. Based on the anomalous patterns previously discussed, the assessment of the email local part helps detect attempts to create fake accounts:
A high number of special characters, which includes the dot (.), underscore (_), and dash (- )
Use of plus/sub addressing method
Low alpha- to- digits ratio
Low vowel- to- consonant ratio
Excessive number of consecutive vowels or consonants
Unusual alpha and digit pattern
The WhoIs method
Whois is a query and response protocol used for querying databases that store an Internet resource’s registered users or assignees. Whois is available as a command line on all Unix/Linux operating systems. When comparing the output of the Whois query for legitimate email domains to the disposable ones, there are two striking differences:
The registration date: For legitimate domains, the domain was registered decades ago when the Internet became a thing, whereas, for disposable domains, it was registered within the last three years or less. Some disposable domains on some websites were registered within a month.
The registrar name: Fraudsters gravitate toward registrars that offer domain registration at low cost, while corporations use more established registrars that offer full brand protection.
An can be seen in Figure 7, the creation date was recent at the time of the research, the domain used the "cheaper" .xyz TLD and is registered with Namecheap.

Fig. 7: Output of the Whois command on a disposable domain
Looking for anomalous traffic patterns on email domains
Being able to recognize unusual traffic patterns in the various email domains is key to helping identify account opening abuses. Figure 8 shows the distribution of account creation using email addresses from a major email service (Gmail.com) over seven days. We see a regular circadian pattern (traffic that peaks during the day and decreases at night), which is the expected traffic pattern from legitimate user activity.

Fig. 8: Account creation pattern with emails from the domain Gmail.com
In contrast, Figure 9 shows account creation with emails from the icloud.com domain. The circadian pattern is somewhat visible but dwarfed by occasional sharp traffic spikes, reflecting short attacks using the popular email services. By using email addresses from a popular email service, the attacker aims to make it harder for the defender to identify the fake accounts.

Fig. 9: Account creation pattern with emails from the domain icloud.com
The pattern of account opening with emails from uncommon domains looks drastically different. Figure 10 and Figure 11 show activity with uncommon email domains like cantuenza1.com or cpzmars.com, with short activity spikes. Both domains are registered with Squarespace Domains, which offers cheap domains with free WHOIS privacy that, in this case, helps hide the attacker’s identity.

Fig. 10: An account creation pattern with emails from the domain cantuenza1.com

Fig. 11: An account creation pattern with emails from the domain cpzmars.com




Comments